

This edition of the SOC case files showcases how Barracuda Managed XDR detects a breach via a ‘ghost’ account and an unprotected server.
The SOC is part of Barracuda Managed XDR, an extended visibility, detection, and response (XDR) service that provides customers with round-the-clock human and AI-led threat detection, analysis, and mitigation services to protect against complex threats.
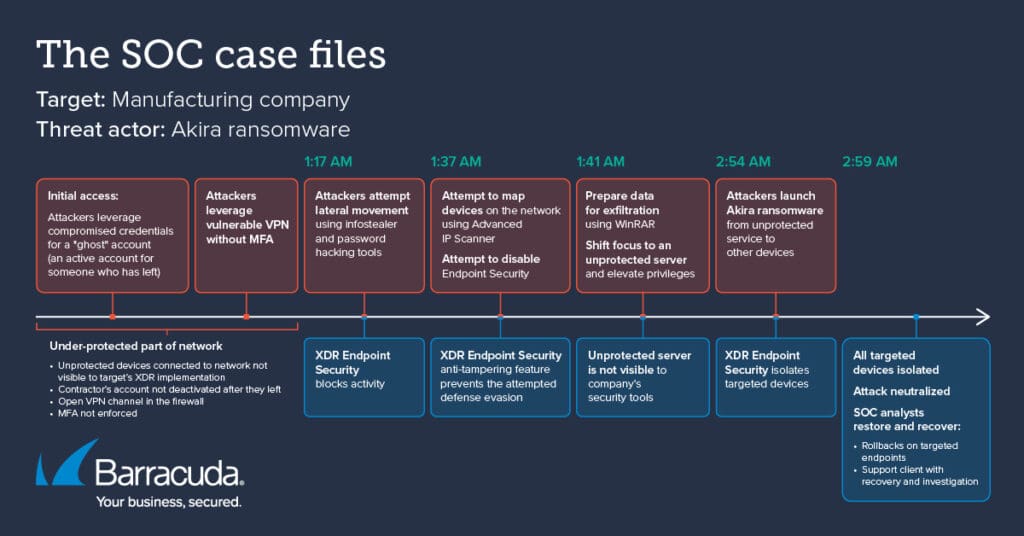
Incident summary
- A manufacturing company fell victim to Akira ransomware in the early hours of the morning.
- The attackers breached the network through a ‘ghost’ account (an account that was created for a third-party vendor and not deactivated when the vendor left).
- At 1:17 a.m. the attackers broke cover and tried to move laterally and disable endpoint security — Barracuda Managed XDR blocked both attempts.
- They then moved the focus of their activity to an unprotected server, elevating their privileges and launching the ransomware at 2:54 a.m.
- By 2:59 a.m., XDR neutralized all impacted devices.
- SOC engineers worked with the target on recovery and investigation.
How the attack unfolded
Exposed areas in the target’s IT environment
- There were several preexisting areas of risk in the target’s IT infrastructure and security policies that increased their vulnerability and the chances of a successful breach. These included:
- Unprotected devices on the network.
- An open VPN channel in their firewall.
- The business does not enforce multifactor authentication.
- The company did not deactivate the account created for a third-party vendor when the vendor left.
- At some point before deploying the main attack, the threat actor got hold of the credentials for the third-party ‘ghost’ account and used this to connect via an open VPN channel to gain access to the network.
- It is worth noting that the additional implementation of XDR Network Security would have detected suspicious VPN activity and helped block the attack at an earlier stage.
The main attack
- XDR Endpoint Security first detected the threat actor at 1:17 a.m. as they tried to move laterally across the network using information stealer malware and a hacking method that can circumvent passwords to gain access to a computer system (known as the pass-the-hash technique).
- Both techniques were successfully mitigated by XDR Endpoint Security. Suspicious lateral movement is one of the clearest indicators of a ransomware attack. In 2024, 44% of unfolding ransomware incidents were spotted during lateral movement.
- The attackers persevered. When they realized that devices throughout the network had endpoint protection deployed, they retaliated in two ways.
- First, at 1:37 a.m., they ran a tool called Advanced IP Scanner to find and list all the devices on the network. Next, they tried to execute commands to disable XDR Endpoint Security, which failed thanks to XDR’s anti-tampering capabilities.
- A few minutes later, at 1:41 a.m., the threat actor began running a tool called WinRAR to prepare data for exfiltration. WinRAR can open most file types and is used for compressing and decompressing files to make the process of downloading them faster and easier.
- At the same time, the threat actor shifted the focus of their attack to an unprotected server where they planned to continue their attack away from the visibility and restrictions of the installed endpoint security.
- The attackers were able to elevate their privileges to the administrator level from the unprotected server and leverage that to execute the attack. If the server had XDR protection, XDR would have flagged the suspicious administrator activity.
- The threat actor released the Akira ransomware just over an hour later, at 2:54 a.m. Akira is a prolific ransomware-as-a-service (RaaS) offering that emerged in 2023.
- The attackers first executed the ransomware on the unprotected server and then tried to remotely encrypt devices they could reach through the network. Remote encryption is a common tactic that threat actors use to bypass security controls that might be activated if they try to execute the ransomware on each individual host.
- However, as soon as the remote encryption process began, XDR Endpoint Security’s custom STAR rules detected the malicious activity and isolated the targeted endpoints from the network.
- Within four minutes, by 2:59 am, XDR disconnected all targeted endpoints from the network.
- Shortly thereafter, the XDR SOC team issued a high-risk security alert to the organization and called them to inform them of the case.
Restore and recover
- After neutralizing the incident, the SOC’s endpoint security engineers investigated the incident and helped the target with recovery.
- The SOC team leveraged XDR Endpoint Security to issue rollback commands to the targeted endpoints and restore them to their latest snapshot from before the incident.
- The post-incident investigation revealed the open VPN channel in the firewall and the lack of consistent enforcement for multi-factor authentication (MFA).
The main tools and techniques used in the attack
| Attack activity | Tools, tactics, and techniques |
| Initial access/intrusion | Compromised account credentials used to authenticate to VPN |
| Lateral movement
|
‘Pass-the-hash’ and Syskey queries to steal credentials to move across the network |
| Discovery | Used Advanced IP Scanner to detect all the devices on the network |
| Attempted data exfiltration | Deployed legitimate file opening and compression tool, WinRAR |
| Defense evasion
|
Executed commands to try to disable installed endpoint protection |
| Main attack execution
|
Attempted to encrypt by executing Akira ransomware |
Indicators of Compromise detected in this attack (SHA1 hash values):
- 66930dc7e9c72cf47a6762ebfc43cc6a5f7a1cd3
- b29902f64f9fd2952e82049f8caaecf578a75d0d
Lessons learned
This incident illustrates how cyberattacks have become increasingly multi-stage and multi-level, with attackers pivoting and adapting to changing or unexpected circumstances while hunting down and exploiting any unprotected and exposed areas.
The best protection against such attacks is comprehensive, layered defenses with integrated and extended visibility.
This should be accompanied by a robust focus on cybersecurity basics. For example:
- Always enforce MFA, especially on VPN accounts that are accessible externally.
- Implement a password policy to rotate credentials regularly to avoid stale passwords.
- Regularly audit active user accounts and disable any that are no longer in use.
In this case study, incomplete security coverage allowed the threat actors to gain access to the network and remain under the radar until they moved laterally. It also enabled them to prepare and launch different phases of the attack from a device that security tools couldn’t scan or monitor.
XDR-protected endpoints, mitigated and remediated every attempt to progress the attack within minutes.
XDR can help in other ways, including:
- XDR Endpoint Security proactively provides data on unprotected devices, helping organizations identify devices on their network without endpoint security deployed, which attackers could potentially exploit.
- Extending XDR coverage to network security could have detected suspicious VPN activity at an earlier stage of the attack. XDR leverages SOAR (security orchestration, automation, and response), ensuring the system blocks the malicious IP address used by the attackers automatically.
- Extending the XDR coverage to include server security could have detected the unusual activity. It would have flagged the privilege elevation that was quietly taking place on the server.
Barracuda Managed XDR includes features like threat intelligence and Automated Threat Response for comprehensive protection. The integration of solutions such as XDR Server Security, XDR Network Security, and XDR Cloud Security helps drastically reduce dwell time.
For further information: Barracuda Managed XDR and SOC.
This article was originally published at Barracuda Blog.

Photo: valiantsin suprunovich / Shutterstock
This post originally appeared on Smarter MSP.

