Hey there! Today, we're diving into the wonderful world of passkeys. Don't worry, this isn't rocket science – my mission is to show you how ridiculously easy it is to get passkeys up and running in your tenant. Sure, standard MFA is a solid starting point, but let's face it - it’s not exactly the finish line of cybersecurity greatness.
So, what are passkeys, you ask? Think of them as passwordless VIP pass into your apps. Instead of juggling passwords, passkeys use cryptographic key pairs to get you logged in safely and securely. Your private key is on your device, while the public key hangs out with the service. Together, they create a phishing-resistant fortress of login magic.
Step 1: Turning on Passkeys
First things first, we’ve got to enable passkeys for users. In Entra, just head over to Protection > Authentication Methods and select Passkeys. Easy, right? If you’d like to roll it out gradually, start with a pilot group—like my creatively named Passkey Pilot Group.

Step 2: Configure Those Options
Time to tweak a few settings! Head over to Configure, and let’s break these down:
Allow self-service setup: Let users set up their own passkeys. Saves you from playing tech support all day.
Enforce attestation: Want only trusted devices in the mix? This setting ensures devices prove their authenticity.
Enforce key restrictions: Want a little more control? This lets you decide which FIDO2 keys are allowed or blocked.
Restrict specific keys: Choose whether certain keys get the red carpet treatment or a big ol’ “Access Denied.”
Microsoft Authenticator: Automatically handles AAGUIDs (don’t worry, just think of it as tech magic) for iOS and Android Authenticator apps.
For this setup, we’re using Microsoft Authenticator, but you can totally swap in FIDO keys if that’s your vibe. Pro tip: This is handy link to identify AAGUIDs for other popular keys.

Step 3: User Setup
Now, the fun part! Direct your users to aka.ms/mfasetup and tell them to click Add sign-in method. Select Passkey and follow the prompts. It’s as simple as opening the Microsoft Authenticator app, creating the passkey, and they’re good to go.
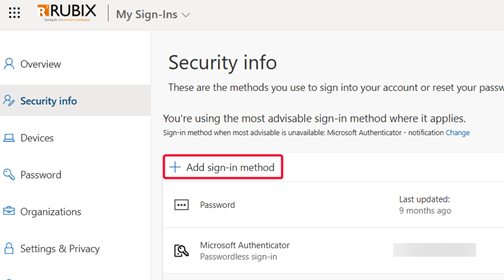
Select Passkey and follow the on-screen instructions.

Part of this next step will direct you to open the Microsoft Authenticator application on your device. Create a Passkey in the Authenticator application.
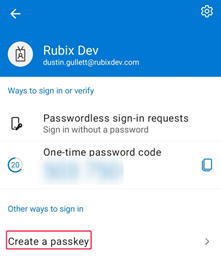
The user will be prompted to Sign In.

Once the passkey is created, select Done.

Back on the users PC, they should receive a notification that their passkey is now created.

Pro Tip for Admins
Here’s where things get serious (but not too serious): Make sure your admins are using passkeys, too. You can quickly lock this down with Conditional Access Policies to require phishing-resistant MFA for all admin activities.
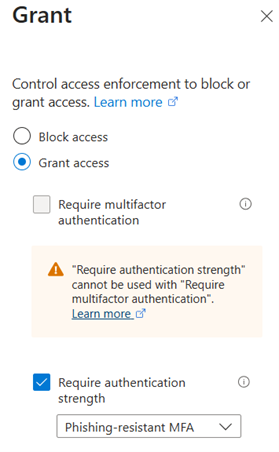
And That’s It!
See? Just a few quick steps to make your users more secure and less stressed about passwords. Go ahead and give it a try, you’ll feel like a cybersecurity superhero in no time.
This post originally appeared on Rubix - Solving for the Modern Workplace.
