

 Barracuda recently launched new email protection plans that enable customers to fully defend their email environments with security tailored to their specific needs. Our first post in this series defined and explained the components necessary to defend against modern threats. In this post, we will explore integrated cloud email security (ICES), how it works, and why it is a core component of cybersecurity.
Barracuda recently launched new email protection plans that enable customers to fully defend their email environments with security tailored to their specific needs. Our first post in this series defined and explained the components necessary to defend against modern threats. In this post, we will explore integrated cloud email security (ICES), how it works, and why it is a core component of cybersecurity.
What is integrated cloud email security?
Integrated cloud email security, or ICES, is a comprehensive, cloud-native approach to email protection. An ICES solution seamlessly integrates with platforms like Microsoft 365 using APIs, enabling seamless access to email traffic, user behavior, and historical data. Unlike traditional gateways, ICES integrates without modifying MX records or disrupting email flow, providing real-time analysis and defense against sophisticated email threats. This API-based approach ensures fast deployment and provides continuous protection by leveraging existing or native email security alongside ICES’s advanced detection capabilities.
Gartner defined ICES in its 2021 Market Guide for Email Security, describing it as an API-based integration with a cloud email provider that goes beyond stopping known email attacks. Analysts found that this API integration provided some new advantages:
- ICES solutions work alongside native email protection, allowing companies to augment rather than replace existing defenses.
- API integration makes deployment easier, as there is no need to reroute email or reconfigure MX records.
- Companies can leverage API integrations to add email threat data to other security systems. For example, extended detection and response (XDR) and security information and event management (SIEM) can consume email data and provide greater visibility into the company’s security posture.
ICES was the security response to the exponential growth of email attacks alongside the rapid increase in cloud email adoption. With a true ICES solution, companies have deep visibility into email communications and real-time defense against advanced threats.
Role of artificial intelligence (AI) in ICES
Machine learning (ML): Enables the ICES system to learn and improve from experience without being explicitly programmed.
ML algorithms continuously analyze email traffic and vast amounts of data, learning from patterns and behaviors, allowing for both proactive and adaptive threat detection in real-time.
Natural language processing (NLP): Analyzes email content for linguistic threat indicators.
NLP enables machines to understand, interpret, and respond to human language. This AI layer examines the text data in the email content for cues like malicious language, suspicious keywords, and grammar inconsistencies. For example, it will look at language patterns indicative of urgency or fear, which is common in phishing emails, or flag requests for sensitive information or financial transactions.
Social graph analysis: Evaluates the context of communications throughout the company.
This observes interactions between users and creates relationship and communication maps of the network. These maps allow the system to identify influential users and understand the normal email dynamics of the network. By mapping “who talks to whom,” ML detects impersonation attempts or abnormal communication. For example, an email claiming to be from a CEO but sent from a domain not typically associated with the executive is flagged as potential fraud.
Behavioral analytics and anomaly detection: Monitors user actions for suspicious patterns that can predict malicious intent.
Behavioral analytics continuously monitors user data like login times, device usage, and email interactions. This data helps establish the normal patterns of user behavior, and continuous monitoring allows the system to detect unusual activities as they occur.
Adaptive security: ICES continuously learns from new threats and adapts its detection algorithms, ensuring protection against evolving attack vectors and emerging threats.
Benefits of ICES
Advanced threat protection: ICES employs advanced technologies to identify and neutralize sophisticated threats, such as impersonation, phishing, or business email compromise (BEC), that often bypass traditional security measures. By integrating directly with cloud email platforms, ICES can identify threats across inbound, outbound, and internal email traffic. This comprehensive protection ensures that organizations stay ahead of attackers, even as threats evolve in complexity.
Simplified deployment and management: Traditional email security solutions often require complex setups, such as changing MX records. ICES eliminates this complexity as API integration allows ICES to connect directly with cloud email platforms. Deployment is fast and simple, and protection begins immediately, with no need to reconfigure MX records.
Continuous improvement: ICES uses several types of AI to learn from new threats and adjust threat detection algorithms. This ensures protection against evolving attack vectors and emerging threats. For IT teams, this means less time spent on manual tuning and maintenance and more confidence that their email security remains effective over time.
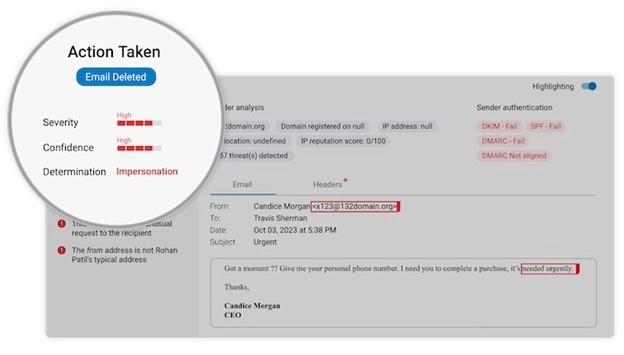
Barracuda’s AI analyzes emails in real-time and takes immediate action to prevent malicious messages from reaching users.
Threats detected by ICES
Phishing and spear phishing: ICES solutions can detect subtle indicators of these threats, even if there is no malicious link or attachment.
Business email compromise (BEC): ICES identifies and prevents attempts to impersonate executives or trusted sources.
Account takeover: ICES uses its established baselines to detect and flag anomalous behavior and other indicators of a compromised account.
Social engineering attacks: Manipulative tactics are detected and flagged, and email users are immediately warned of potential risks.
Credential phishing: ICES automatically blocks targeted phishing emails that try to harvest employee passwords.
Insider threats: ICES detects irregular communications and user behaviors that differ from established norms. These irregularities may indicate malicious or unintentional insider threats.
Invoice fraud: ICES detects irregularities in financial communications and disrupts these attempts to defraud the company.
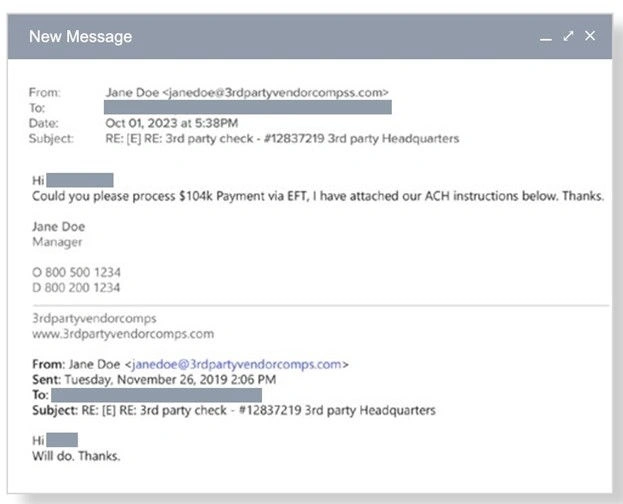
Sample of financial fraud email attack prevented by Barracuda Email Protection. See Top Email Threats and Trends for more examples.
The future of email security with ICES
ICES is more than an email defense system; it’s a proactive and adaptive solution designed to keep up with the evolving landscape. By leveraging seamless integration, advanced machine learning, and continuous learning, ICES allows organizations to stay one step ahead of cybercriminals.
As email threats continue to grow more sophisticated, the role of ICES will expand, with future advancements likely to include even deeper AI-driven insights, predictive analytics, and tighter integrations across the security stack. Organizations that invest in ICES today are securing their present environments and preparing for tomorrow’s challenges.
See how Barracuda Impersonation Protection, which is integrated cloud email security, can help you.
This article was originally published at Barracuda Blog.
Photo: Tete Escape / Shutterstock
This post originally appeared on Smarter MSP.

