Simplifying Secure Access with Microsoft Entra ID Governance
Managing access to critical resources can be a nightmare like trying to keep snacks away from a hungry toddler. You want to lock things down tight, but you also don’t want to deal with endless requests for “just five more minutes” of access.
Enter Microsoft Entra ID Governance and its Access Packages the superhero we didn’t know we needed. These magical bundles let organizations automate access requests while ensuring security doesn’t take a backseat. Think of them as an all-you-can-eat buffet, but instead of food, it’s access to apps, groups, and resources with strict portion control.
But Wait, What About Just-in-Time (JIT) Access?
In a previous blog, I covered Entra Private Access, which lets us assign access to users or groups for specific applications. But what if we don’t want users to have permanent access? What if we need Just-in-Time (JIT) access for high-value resources, like domain controllers?
Since my Microsoft Entra Suite license includes both Entra Private Access and ID Governance, I decided to combine them. This setup lets users request access on-demand (JIT) and securely connect to their on-premises resources only when needed—kind of like a bouncer checking IDs at an exclusive club, except the club is a domain controller, and the bouncer is an access policy.
Let’s break it down step by step.
Setting Up Access Packages for Secure RDP Access
To illustrate how this works, I’ll walk you through configuring an Access Package for RDP access to domain controllers using Entra Private Access.
Step 1: Create a Catalog
First, navigate to Identity Governance > Catalogs. A catalog is essentially a container that organizes Access Packages along with related resources like groups, applications, and SharePoint sites. It allows administrators to delegate access management while ensuring only authorized users can request or assign access.
Instead of adding resources to the default General Catalog, I created a new one called Rubix Administrators. This catalog will manage RDP access to domain controllers and other critical resources (I’ll cover these additional resources in a future post).

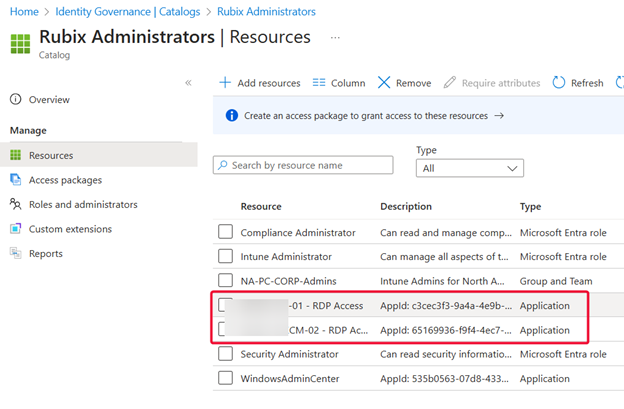
Step 2: Add Resources
Once the catalog is created, it’s time to add the resources that the Rubix Administrators group will need. For this setup, I added:
My Private Access applications for both my Domain Controller and MECM server.
Step 3: Create an Access Package
Now, head to ID Governance > Access Packages to create the actual package.

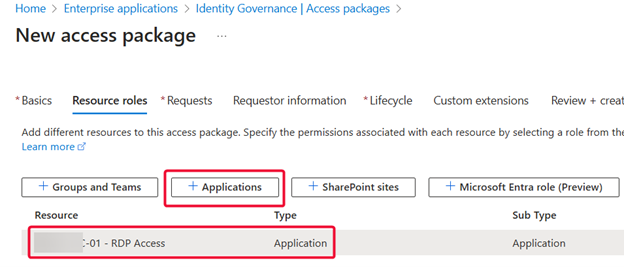
Name the Access Package and select the Rubix Administrators catalog.

Choose Resources: While the catalog may contain multiple resources, for this example, I’m only including my Domain Controller RDP application.
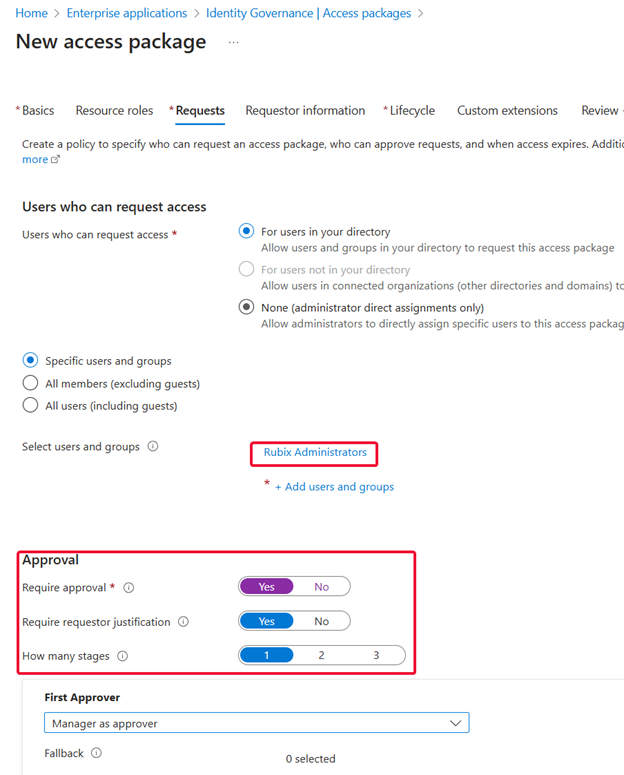
Configure Requests: Here, I add my Rubix Administrators group and define approval requirements.
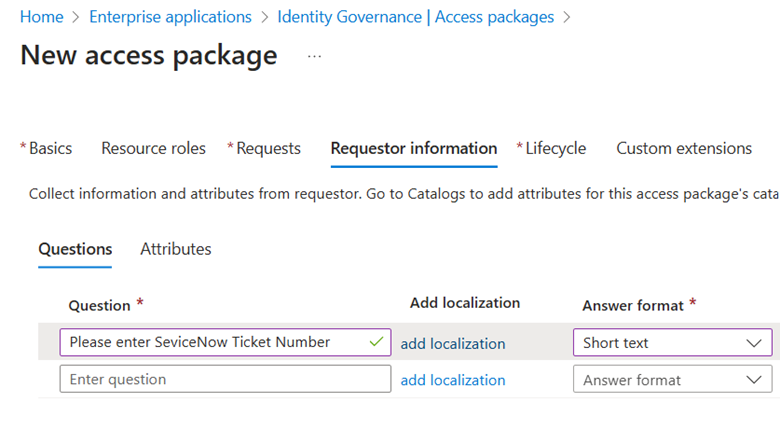
Request Form: If you want to make users sweat a little, you can ask them additional questions before granting access. (Optional, but great for passive-aggressively reminding people that security is serious business.)
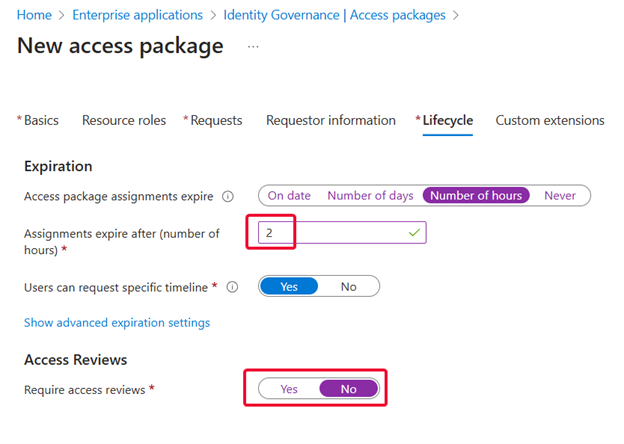
Lifecycle Policies: I set this Access Package to expire after two hours since it grants RDP access to a domain controller.
Access Reviews: Not covering them today, but they’re like those “are you still watching?” prompts on Netflix except for security.
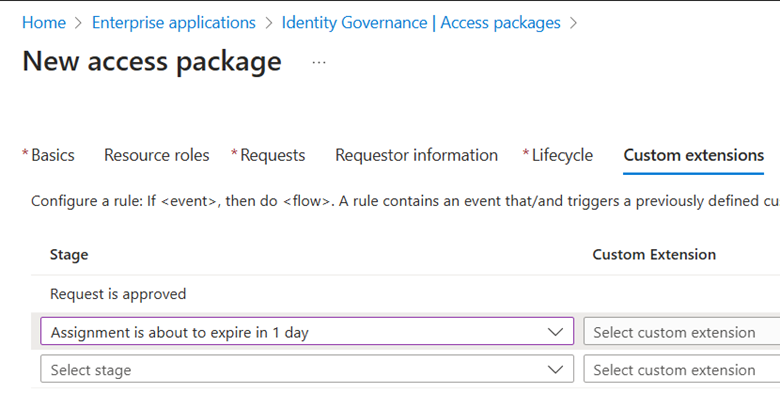
Custom extensions are available as an optional tab. Currently, I do not have any Logic Apps in my test environment, but the Microsoft documentation provides detailed coverage on this topic.
Step 5: Testing Access Requests
Now, let’s test it out!
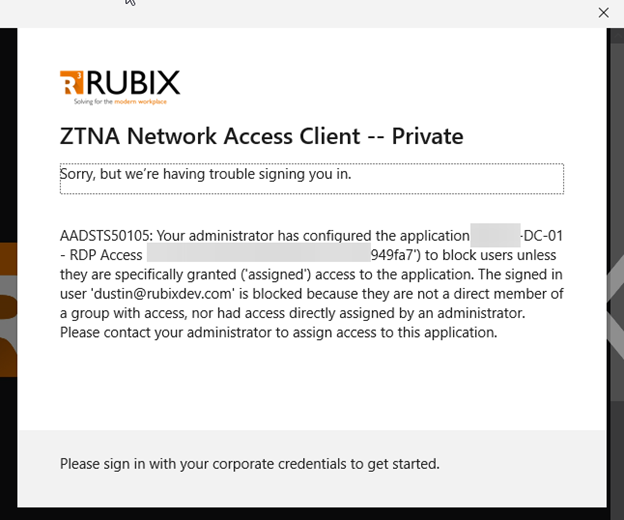
A user attempts to RDP into the domain controller but gets an error expected, since they don’t yet have access.
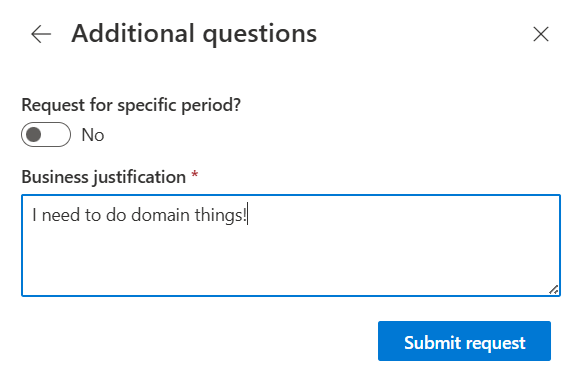
2. The user navigates to https://myaccess.microsoft.com/ and selects the relevant Access Package.

3. If a Business Justification was required during setup, they fill it in.
4. Once the request is approved, the user is automatically added to the required application.
5. The user can now RDP into the domain controller using Entra Private Access.
And the best part? Since we configured a two-hour expiration, access is automatically revoked once time’s up no manual cleanup needed.
Wrapping Up
By combining Entra Private Access with Access Packages, organizations can implement Just-in-Time access without compromising security. Users get the access they need only when they need it, and IT teams stay in control with automated approvals and expiration policies.
Stay tuned, I’ll be diving deeper into Access Reviews in a future post. Until then, happy securing!
This post originally appeared on Rubix - Solving for the Modern Workplace.
