
The threat landscape is always churning, with new threats emerging while others disappear or fade to irrelevance. Consider ALPHV, a ransomware-as-a-service (RaaS) group that provided the infrastructure, tools, and administrative services to the individual hacker who ransomed $22 million from Change Healthcare in February 2024. ALPHV apparently didn’t want to share the ransom with the threat actor who carried out the attack. The group drained their cryptocurrency accounts disbanded, and disappeared into one of the 33 new or rebranded ransomware groups that emerged in 2024. These 33 groups and the 40+ existing active groups appear to represent a 30% increase in ransomware threat actors. Some groups remained intact but turned their attention away from ransomware.
Changes in the landscape lead to changes in the outcomes as well. The average cost of a data breach in 2024 jumped to $4.88 million, up from $4.45 million in 2023. These costs have been increasing since 2018, so there’s nothing new there. The interesting bits are in the details. The breach-related costs to healthcare decreased from $10.93 to $9.77 billion. The average time to identify and contain a breach fell to 258 days, down from 277. Phishing and stolen or compromised credentials remained the top two attack vectors.
Ransomware costs continued their upward trends as well, though fewer companies were paying ransoms. The average ransom payment in 2024 increased to $2.73 million, up from $1.82 million in 2023. The largest known ransom payment was about $75 million. This payment was undisclosed by the victim and is only known to us because it was discovered and confirmed by researchers. This lack of disclosure by the company is one example. It shows why it’s difficult to get a full picture of the costs and other damages from global cybercrime. While we don’t have the complete picture of the threat landscape and its impact, we do have some data. This data provides other interesting insights.
$9.22 – $9.5 trillion
Since we just mentioned the total cost of global cybercrime, let’s start there. There’s no single accurate number for this, but we have some data-driven estimates of the damage.
The most frequently cited cost of global cybercrime is $9.5 trillion. This is an estimate by Cybersecurity Ventures, who has defined the costs as “damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data and systems, and reputational harm.” Using the same definition, Statista’s Market Insights puts the 2024 damage at $9.22 trillion. This is slightly lower than Cybersecurity Ventures, but both expect the cost of damages to increase by another trillion in 2025.
One reason we can’t get a clear picture of the total cost of global cybercrime is that we must consider various factors. Reputational harm is one of these factors. Rebuilding a damaged brand and regaining the trust of consumers and shareholders is a difficult and costly operation. You can measure the lost customers, disrupted sales, and downtime-related costs in the immediate aftermath of a security incident. However, you do not receive an invoice for ‘reputation and brand repair.’Understanding the full extent and cost of the damage requires a long view.
Calculating the cost of cybercrime also relies on accurate reporting, and most attacks are never disclosed to the public or law enforcement. Besides protecting their reputations, some victims simply do not see the point of reporting an incident they can resolve on their own. Others just don’t know who to contact. There are at least 12 federal agencies in the US that collect information on cybercrime, but they do not track and categorize these crimes in the same way. This fragmentation makes it difficult to establish and track cyberattacks.
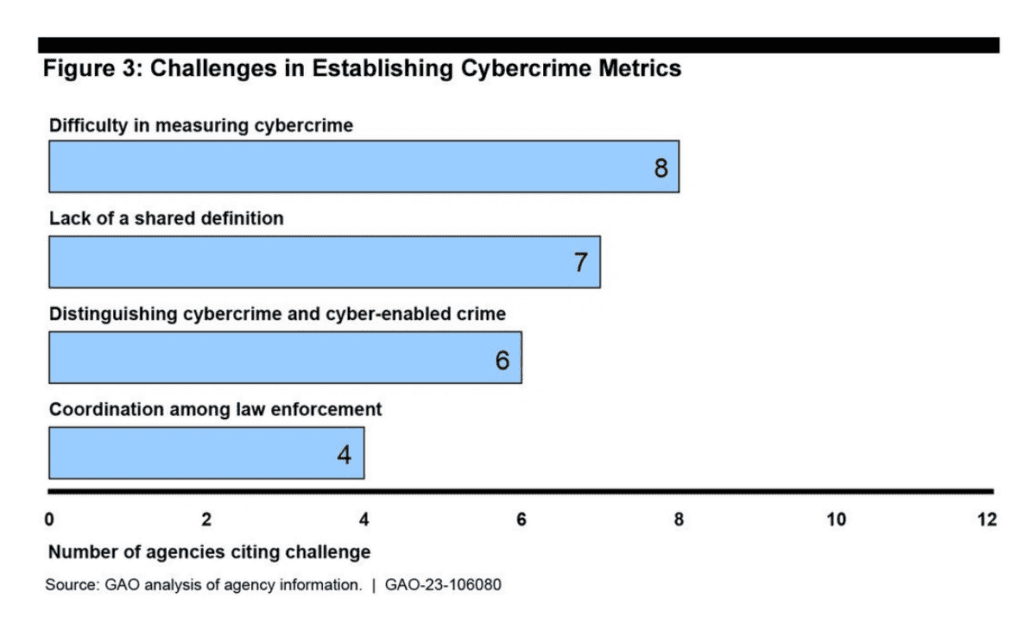
US agencies report challenges in measuring the extent or impact of cybercrime, via the United States Government Accountability Office
Legislative-based efforts are underway to create a standard taxonomy and a centralized cybercrime database. The Secure Our World program is also an example of efforts to raise awareness about fighting and reporting cybercrime.
400 million
Roughly 400 million desktops ended 2024 with only ten months left to live. These systems will lose access to security updates and technical assistance in October 2025, when Microsoft officially ends support for Windows 10. Companies can purchase subscriptions for updates beyond this date, though the price per device will double each year.
Microsoft Windows dominates the world of desktop operating systems, with about 99.93% of the market share across multiple versions. Here’s how it breaks down as of December 2024:
| Windows Version | Market Share (%) |
| Windows 10 | 62.73 |
| Windows 11 | 34.1 |
| Windows 7 | 2.4 |
| Other Windows versions | 0.7 |
Systems older than Windows 10 are already without support. We can assume some Windows 10 devices will join the ranks of the unsupported. Running systems that are not secured is risky, but we know it happens. However, if we assume all desktops will be updated, this could cost companies and individuals over $60 billion. Here’s why:
| Category | Estimated Number of Devices | Assumed Cost per Device | Total Cost (USD) |
| Systems that must be replaced | 48 million (12%) | $1,000 | $48 billion |
| Systems that need a hardware upgrade | 88 million (22%) | $200 | $17.6 billion |
| Extended Security Updates (ESU) | Per Device | $427 (over 3 years) | Potentially billions |
There are also costs associated with updating devices that are compatible with Windows 11. Most modern systems can install Windows 11 in less than an hour, but there are still risks to updating an operating system. Some installations will run into complications with third-party software or drivers. They may also experience data loss and unexpected conflicts with hardware that should be compatible. Even small companies can require significant resources to plan, test, and install Windows 11. Downtime and troubleshooting increase the costs.
40,289
2024 is another record-breaking year for Common Vulnerabilities and Exposures (CVEs), according to any source that tracks them. CVEdetails records 40,289 new CVE publications, which amounts to over 15% of all CVEs released to date.
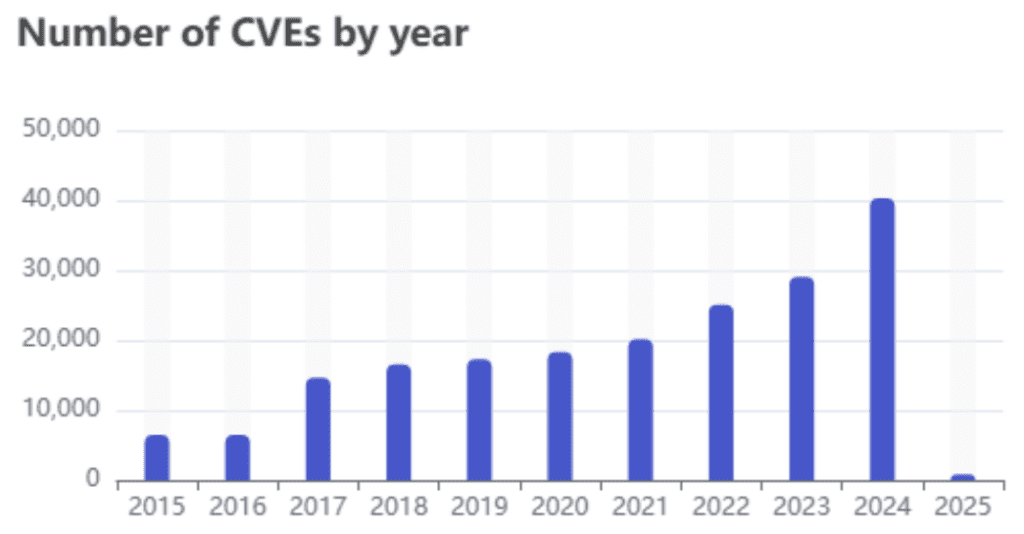
Cumulative Yearly CVE publication, via Cyberpress
Only 204 of these vulnerabilities were weaponized by threat actors, but they were responsible for some of the most significant cyberattacks of the year. For example, exploitation attempts against Ivanti Connect and Policy Secure Web reached approximately 250,000 per day, with attack traffic from 18 countries.
There was also a 10% increase in the exploitation of older CVEs in 2024, which should serve as a reminder that new threats are not the only risk. Organizations must address previously identified vulnerabilities, even if the systems are difficult to patch or replace.
In 2024, threat actors stole $2.2 billion worth of cryptocurrency and other digital assets by attacking decentralized finance (DeFi) platforms and other supporting infrastructure components. About $1.34 billion of this activity was linked to threat groups acting on behalf of the Democratic People’s Republic of Korea (DPRK). DPRK state actors go to extreme lengths to carry out these attacks and deliver the funds to Pyongyang. These funds are used to develop missile programs and other operations and are a key source of revenue for the regime.
Another $494 million was stolen through wallet drainer attacks that use malicious websites, malvertising, and email phishing attacks designed to trick victims into providing access to their wallets.
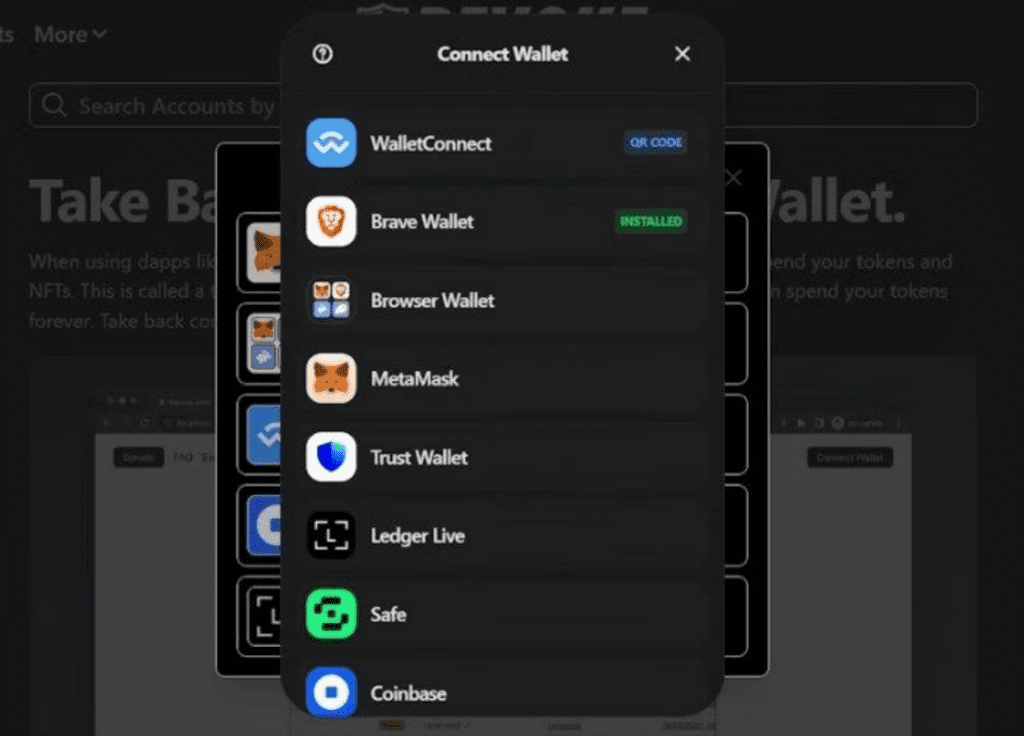
Cryptocurrency wallet drainer popup designed to steal assets from a visitor’s wallet, via Hackernoon
Experts attribute this $494 million to wallet drainers, excluding it from the $2.2 billion lost to platform and infrastructure attacks.
2.4 million
Here’s something a little different. Cyberattacks against Taiwan’s Government Service Network (GSN) and other institutions doubled in 2024, reaching an average of 2.4 million per day. Experts have linked most of these attacks to official cyber operations of the People’s Republic of China (PRC). Taiwan’s National Security Bureau noted that transportation, telecommunications, and the defense supply chain industries are the key targets of the PRC.
Taiwan has made significant investments in cybersecurity and is currently in phase six of a 24-year cybersecurity plan.
Illustration of phase 6, National Cyber Security Program of Taiwan
The United States and Taiwan have a strong relationship in terms of cybersecurity resiliency, including the adoption of shared frameworks, joint cybersecurity/cyberwar exercises, and the sharing of defensive cybersecurity assets. This partnership has become increasingly important in recent years because of the escalating cyber threats faced by Taiwan, particularly from China. The US has also noted that PRC attacks on US companies are often tested first against targets in Taiwan.
105,120
There were 105,120 deepfake attacks reported in 2024, which is about one attack every five minutes.
A deepfake is a sophisticated form of synthetic media that uses artificial intelligence (AI) and machine learning (ML) techniques to create or manipulate audio, video, or images. The finished media product is completely fake but highly convincing, and it is used to spread misinformation and facilitate fraud.

Proof of concept deepfake video created to warn the public about disinformation, via Europol
Most deepfake attacks targeted the financial sector, with 9.5% specifically targeting cryptocurrency platforms. Lending, mortgages, and traditional banks were also among the top financial targets, at 5.4% and 5.3% respectively. Total losses to the financial services sector exceeded $603,000 per company. 10% of all deepfake victims reported losses over $1 million.
Threat actors have many ways to weaponize deepfakes. Google DeepMind recently mapped the goals and strategies of deepfake threat actors:
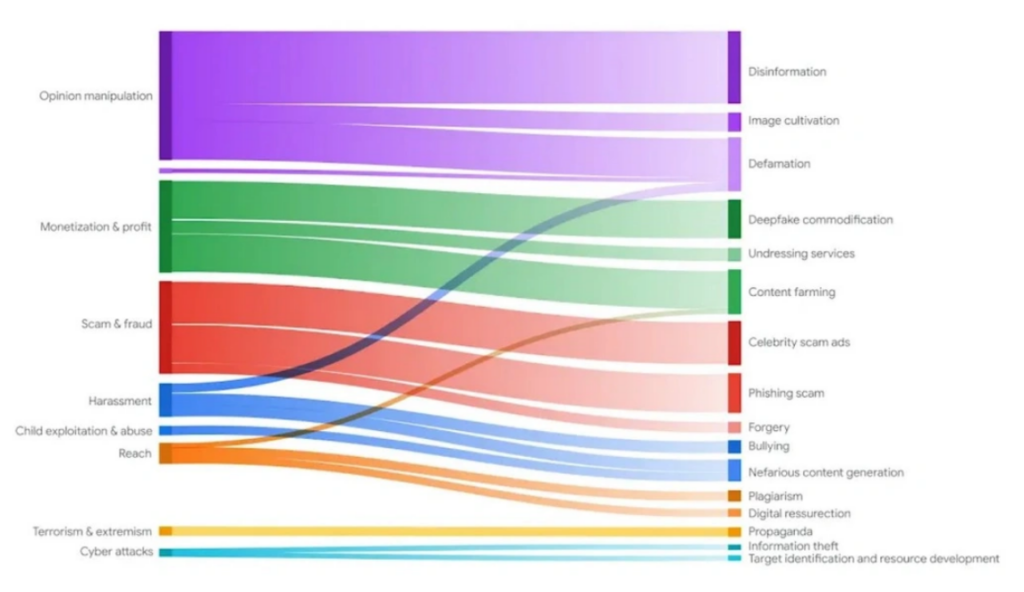
Diagram of how the goals of bad actors (left) map onto their strategies of misuse (right), via Google DeepMind
Cybersecurity experts are warning that deepfake financial fraud could be the next major fraud trend in the United States and other Western nations.
Cybercrime reached unprecedented levels in 2024 and continued to outpace defensive measures even though global security spending reached approximately $215 billion. Cloud environment intrusions and malware-free attacks like social engineering surged, and DDoS attacks were significantly higher than in previous years. Malware attacks against IoT devices, primarily in manufacturing, increased by 400%.
While we can’t get the complete picture, we can extrapolate from what we see here. World events are changing the threat landscape. Geopolitical tensions and political divisions are now as relevant as the desire for financial gain. Companies, governments, and other organizations have to remain vigilant against these attackers. And of course, all victims should report cybercrimes to law enforcement officials.
This article was originally published at Barracuda Blog.
Photo: Tete Escape / Shutterstock
This post originally appeared on Smarter MSP.



